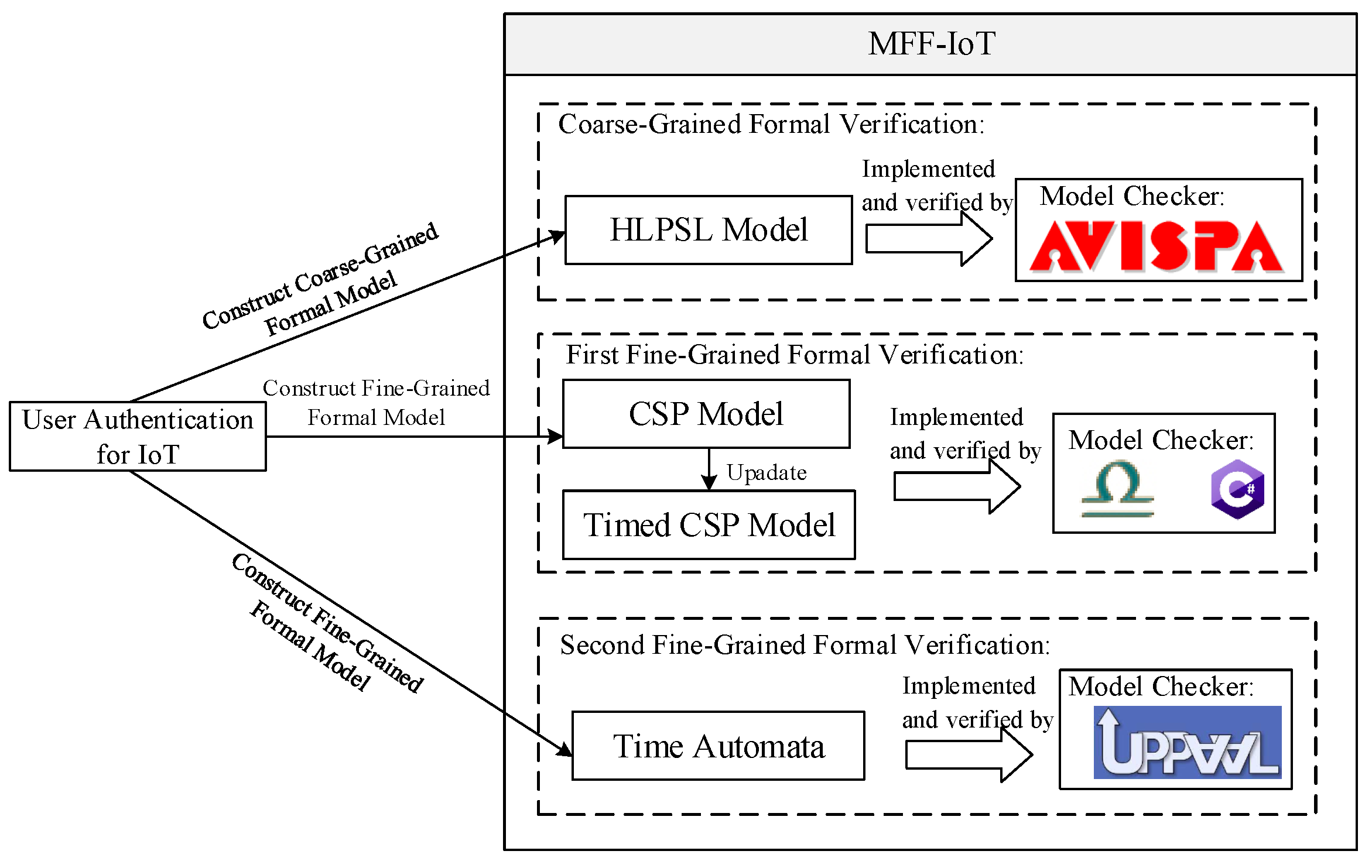
Electronics | Free Full-Text | MFF-IoT: A Multi-Granularity Formal Framework of User Authentication for IoT

A blockchain-based keyword search scheme with dual authorization for electronic health record sharing - ScienceDirect

How Dare They Peep into My Private Life?”: Children's Rights Violations by Governments that Endorsed Online Learning During the Covid-19 Pandemic | HRW

Buildings | Free Full-Text | Integrating Information Entropy and Latent Dirichlet Allocation Models for Analysis of Safety Accidents in the Construction Industry

What is accounting fraud detection? AI-based detection methods and effectiveness explained | Solving forensic investigations and e-discovery with AI | FRONTEO, Inc.